Video Transcription
0:09
[Greg] Okay, so welcome, everybody. Thanks for joining this is our inaugural first meeting where we’re going to have a discussion around cybersecurity. It is sponsored by IronNet, who’s building this dome for the Australian sector.
And so we really wanted to get some experts on the field to be able to talk about “what does Iron Dome look like” in other parts of the world, and more importantly, how we’re seeing the security landscape and how it affects the Australian care and community sector.
My name is Greg Clarkson. I’m the CEO of Network Overdrive, and I’m a partner of IronNet. And I’ve got two representatives. I have Joel, who’s all the way over in the US, and also Paul Davidson, who is with me in Australia on the ground helping the various communities here. How are you doing, Paul?
[Paul] Good. Thanks, Greg. Thanks for setting this call up.
[Greg] We wanted to start because in the media, we’ve seen a number of incidents. Joel, can you give us some more details about what’s happening with ransomware? in the industry, and in particular, there’s a rabid gang that seems to be claiming responsibility?
1:16
[Joel] Yeah, we are seeing REvil ransomware that revolt groups specifically around the globe, including the US. Now, it’s really interesting to see this group because originally REvil ransomware, they excluded us organizations from the ransomware campaigns.
One of the articles mentioned how the uniting care Queensland was impacted by this ransomware attack. It was assumed to be the REvil ransomware group. And it talks about them increasing process controls, and one of the things that they were doing was implementing a market leading endpoint detection and response solution to help provide ongoing protection. So it’s really interesting, and you know, I’m glad they’re implementing additional controls.
I guess my question, and the reason for this webinar, Greg, is, is that enough to stop these attackers?
[Greg] That’s right, exactly. It’s like some people might say, our EDR. That’s it. Job done. We can move on. What’s your answer to that? Is that enough for what else needs to happen?
2:17
[Joel] Yeah, so we’ve been tracking a number of these ransomware groups and just threat actor groups in general. Right. And it’s, it’s really interesting, because we see the US government, we see governments around the world saying, this ransomware problem is the biggest threat.
But when you kind of break apart the ransomware, problem, ransomware is the end result of a lot of different cybersecurity decisions that you take as an organization. Right? So they’re, they’re exploiting numerous things, right?
It comes down:
- “Are you running endpoint detection response?” If you are great,
- “how’s your patch management?” Right?
- “What are your network defences look like?”
And because once they get in through, you know, numerous different ways, then they get that to spend that time in your network.
And a lot of that stuff, your Endpoint detection response (EDR) will not pick up. So it is an interesting one.
[Greg] Really?
[Joel] Absolutely.
3:05
[Greg] Can you give an example of that? Have you seen something where someone had a great endpoint detection, and yet they didn’t detect one of these attackers?
3:15
[Joel] One of the big ransomware attacks that hit the states recently was the colonial pipeline.
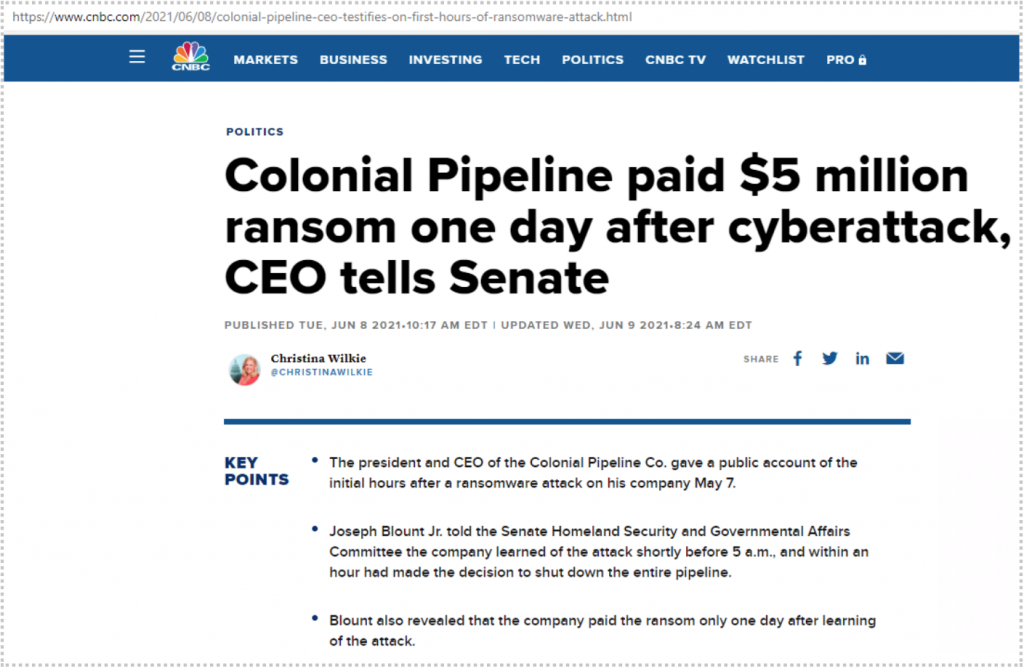
And I’m sure you guys heard of that one. Shut down oil to the eastern coast of the EU, you know, US seaboard where I live, people were freaking out, filling up bags with gasoline, because they were really nervous about this, right. So I’m going to go ahead and bring up one more picture for you.
This was an article done by Sophos, and actually walked through all of the different tools this threat actor group used.
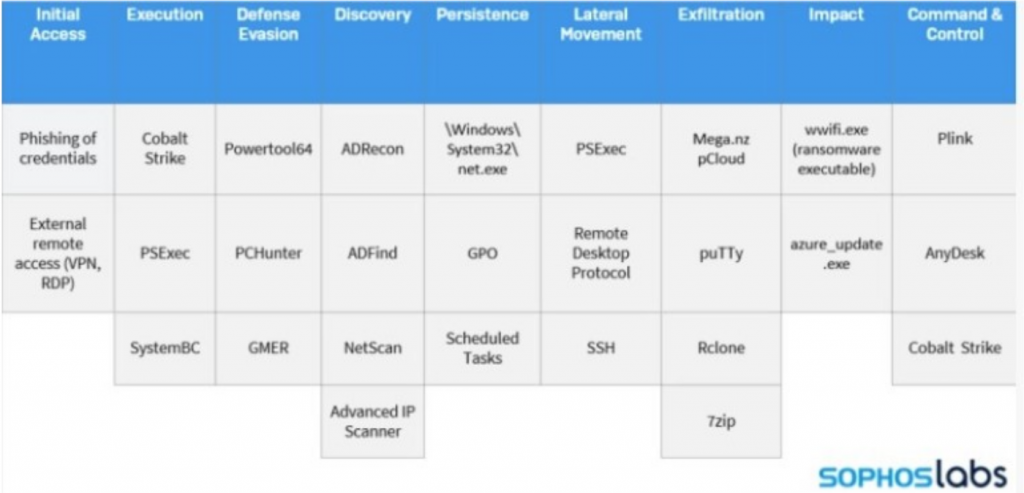
Now, there are some things on the endpoint that you can see, right? scheduled tasks, seven zip, right. So there are some certain processes. And most of these are common tools that are used by other software as well. But when we talk about the chain of attacks, man, Greg, I’m telling you, there’s a lot from cobalt strike beacons to IP scanners to different PS exec, right. So these are things that typically your endpoint isn’t going to alert on. These are behaviours over the network that aren’t detected through those endpoint detection and response tools.
4:24
[Greg] Excellent. And I imagine, Paul, you’re seeing this as well from your role.
4:30
[Paul] Yeah, so we’re seeing, you know, this type of activity increasing, right. So when you when you go back a number of years, looking back, you may see snippets in the news of different cyber-attacks. But I think since you know, COVID, and the last couple of years, we’re seeing this accelerate, right?
So we’re seeing that our own government are starting to highlight the risks of cyber-attacks on organizations. They’re increasing their funding, [being] organize, you know? [From] the news articles, it’s like a weekly, almost daily event that we’re starting to see cyber-attacks in this region in news.
And it’s definitely a topic at the moment that’s at the top of the list, right? So, you look back at organizations, they typically spent their budgets on IT and security tends to be the last afterthought when it comes to looking after your organization.
But I think, you know, talking to different enterprise here in Australia, and as you mentioned before, in the region, in New Zealand, we’re starting to see a real big focus on cybersecurity, because it’s now starting to impact, you know, you’re starting to know organizations that, you know, you’re directly connected to, in your ecosystem or across your supply chain, that are getting hit by these cyber-attacks.
5:55
[Greg] What I noticed and another article that I was following in search security. Firstly, it was very scary to read that those who actually pay a ransom where 80% of them get hacked again. But even those who don’t pay the ransomware, if it was successful, there’s been an increase, attempts to let go even harder, and to leverage perhaps with a sale of data on those organizations that don’t pay the ransomware.
And in the same article, which is the main point that I wanted for us to discuss about now, it talks that, for those who have been hit by ransomware, they tend to spend their money in fixing the problem in five areas.
- The first one is security training awareness.
- The second is establishing an actual SOC (Security Operations Centre).
- The third is the endpoint protection, which is what we’re talking about right now.
- Fourth is backups and recovery.
- And the fifth is in some sort of email scanning.
I’m just interested, Joel, if you could go back and pull up that diagram of all those other attacks. Is there anything that jumps out to you that is not covered by someone who’s investing in these five areas?
7:10
[Joel] Yeah and let me and I’d love to do that. Greg, let me do that here in a moment. You know, I really want to dress. First of all, those areas are an excellent foundation. Right? I mean, here’s the reality is, yes, you have to do those things.
But what that clearly shows me is that these organizations are a decade behind already. Yeah, that’s a huge issue. I mean, you’re just now deployed endpoint detection response? “What were you using free antivirus before that?” you know, it’s like, these basic cybersecurity constructs that have been around for decades now are just now being implemented.
So let me pull up that diagram for you. Because when we walk through some of the ransomware tools from the darkside group, and now you have to remember a lot of these ransomware groups are using similar TTP, or tactics, techniques and processes.
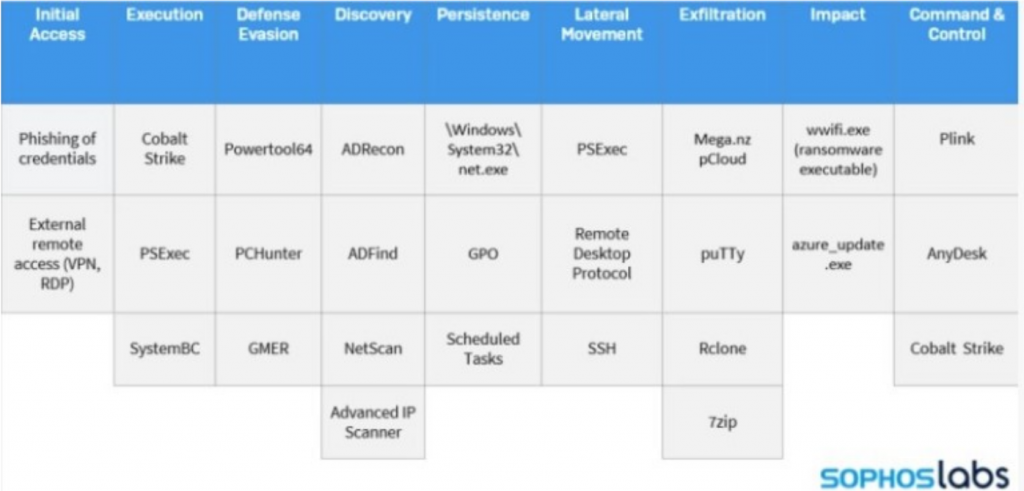
But you have that initial access, right? So the security awareness training, it covers this, right, the phishing of credentials, that’s one of the five [investments], but you can see there’s a lot of other tactics and techniques used, right? So, when we talk about things that aren’t going to be covered by your endpoint detection response, a lot of the discovery phase, you’re not going to see any of that, right, because that’s all done on the network, where they’re a numerating your process [and doing] a lot of this lateral movement, none of that is going to be picked up [by EDR].
Now there are some endpoint detection response tools that say, Hey, we can detect some networks, right, we have this moved to NDR. Which is kind of next step, because you have to gain visibility into your network, the network detection response part is going to be key for some of these, then you have things like exfiltration, and command and control. A lot of those are not going to be seen on the endpoint, right? You could take solar winds, for example. They were doing C to DNS tunneling off solar winds, Orion boxes, but they can test it against these endpoint. I mean, they test their malware against these endpoint detection response tools, long before they ever deploy it. Right. So it’s really an interesting dilemma to see.
9:07
And that last one you talked around, they started to build in the smarts to actually check your systems for those endpoint security tools, and turn them off. So you know, those, as you mentioned before, those tools are great. They are one part of visibility across your enterprise. By bringing the network piece together with the endpoint, it’s giving you better visibility across your enterprise. Plus, there’s not all devices or peripherals that you can actually put into endpoint security onto as well, right.
[Paul] So what if they compromise something that you don’t have the security tools looking at, you can then have a second layout to capture and get better visibility or stitch them together, right? I’m seeing this occurring on the endpoint. What am I seeing on the network and you get better visibility around That tag, right. And those adversaries are going to give you little subtle hints that they’re inside your environment. So if one misses, it’s very hard to hide on that network layer.
10:12
[Joel] Just to piggyback off that I just pulled a quick picture off Google real quick. I wasn’t planning on sharing this, but this is the SOC visibility triad. Right. So you talked about those five things, Greg, that they’re investing in, right? security awareness training, awareness training, it’s a necessity, right? They’re standing up a SOC, and then they’re investing in EDR?
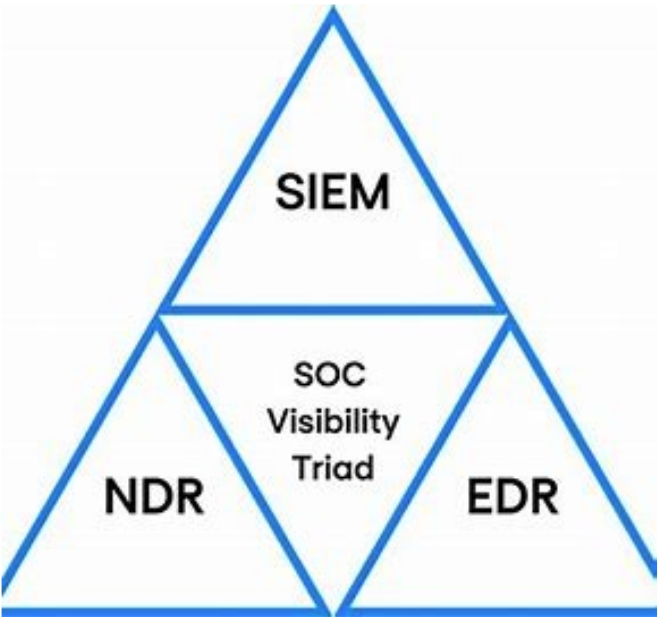
Yeah, well, there’s a couple other parts to this SOC visibility triad, you have to be able to aggregate and ensure visibility over the things you’re responsible for. That’s where the sim portion comes in. But the other portion is this MDR. Right. So we’re seeing a great baseline been set for these organizations. But it’s time for us to take the next step and build this defence in depth. The way it’s meant to be.
10:58
[Greg] Awesome. Do you mind breaking out all those letters just in case there’s someone who is not sure what EDR [means]? Is it endpoint defence? What are the other ones?
11:07
[Joel] Yeah, that’s a great question. So once again, I work here at the cyber operations centers as a senior threat hunter here at IronNet. But these are required, right, even in our own SOC .
So EDR is endpoint detection and response, right? So you have an agent on every single device that you’re responsible for.
The SIM is where you collect all your log data, right? And you can analyze it think, a Splunk or a logarithm, and then your MDR is your network detection response. Right?
So picture this, you have your firewalls, they’ve been around for a really long time, your endpoint detection and response. And you’re aggregating all that data into your Sim, right? So really, you have your perimeter and your endpoint. But what about all this stuff in the middle? That’s where the NDR fits in. And that’s why you have to have it in order to fulfill this SOC visibility triad.
11:57
[Greg] That’s awesome. And so unfortunately, there was another organization, this time in New Zealand that hit the news, also with a ransomware. That was really crippling [as for] three weeks they were unable to develop [and] deliver services. And apparently another actor claimed, well, no one’s claimed responsibility officially. But the behaviour seems very similar to a group that’s called the Contilocker. I’m not sure if I’m saying that right. Maybe they haven’t even pronounced it themselves to correct me? [Anyway that] gang that hit them with another attack. Has Ironnet been aware of this organization, this “MO”, modus operandi that they’re doing, and they brought down this health care service in New Zealand?
12:45
[Joel] Yeah, so we’re tracking most of the major ransomware gangs? And so the answer is yes. Right.
And the hard part is, a lot of them have similar “MOs. Right. At this point, ransomware gangs are very financially driven. And I think it’s really interesting, because as we move on, we continue to say, shouldn’t we not pay this ransom? Like, if we quit paying the ransom, won’t they quit operating?
Well, it’s really interesting, because here in the US, and maybe you can give us some insight on any Australian legislation, that’s being discussed, and we’ve talked about making it illegal to pay the ransom. In groups like Conti and REvil, they’ve actually said, “That’s not going to deter us one bit” (referring to any US legislation created). So I’m curious, Greg, from your perspective, hey, do you think we should be paying the ransom? And B, do you think if we make legislation that people will stop paying the ransom, if they’ve locked up something that is of essential business need?
13:48
[Greg] Well, I don’t think you should pay the ransom, [but for] private companies it is very difficult. I definitely see, you know, the small business, who can’t run their operation, they haven’t got good backups, and a $10,000 fee for the hard chance to get half their data back. They’re willing to pay it. And so that they don’t know how to use Bitcoin or whatever. But they’re still willing to pay it and just take the risk.
Public Organizations, healthcare services, anything that’s funded by the government, they shouldn’t [pay] but again, now you’re talking about people that, if they can’t deliver a service, perhaps someone’s life is at stake, and [they’re] going to suffer? So it’s a very difficult choice, [and] I don’t want to sit in judgment on anyone that says [pay it], but I think it does perpetuate this [activity].
What they say, maybe this is what you’re referring to Joel, is that even if you choose to not pay the ransom, if they’ve got in, they tend to not do the ransomware until the last moment where they [are] making their public disclosure that they’ve got in and they’ve collected data from you. They’re collecting all the valuable information they can prior to the ransomware. And then if you don’t pay the ransom, they can still make their money on selling that data on the dark web. What do you think about that Joel?
15:16
[Joel] Well, I think it’s really interesting. And I gotta bring that around, Greg to the one of the first points you talked about which was that a lot of these organizations get double-tapped. That’s what I call anyway. They pay the ransom. And guess what, because they don’t have that SOC visibility triad. And they’re not doing a full-blown incident response and really cleaning and starting fresh. The [Ransomware Gangs] still have hooks in their network, right, and they can come back and double-tap. And then on top of that, oh, by the way, they already have all your data. Now, Greg, I probably should have discussed what a few of the pictures I had teed up for today. But do you remember hearing in the past that advanced threat actors have a certain amount of dwell time in your environment?
15:56
[Greg] Yeah, exactly. I was hoping you could explore that more. So I think most IT professionals are aware of this, but the media just announced this event, like “Oh, so and so has been ransomware”, then you wait a couple of weeks, and then [what] you hear in the media is, “oh, they’ve now recovered from backups. And they’ve implemented a solution”. And you [as a reader] can just move on [and not think about it anymore].
But I’m not seeing in the public domain is many people talking about “How long have these guys been in your network before the ransomware event actually happens?” It could be six months. Do you [know]? What information do you have about that?
16:35
[Joel] Yeah, that’s a great question. So first of all, it depends on the region of the world, right? I think here in the US, we have a little bit shorter dwell time, right, according to these cybersecurity companies in the media, than what Oceania does. That we actually found out and once again, this was from some really good due diligence done by Sophos, but they actually took a look at the dark side group, and the numbers out there, like they have 180 days, which is six months or more dwell time in your network. And the reality is, they no longer need that much time in your network.
[Greg] Hmm.
[Joel] What’s happening is that for the Darkside group, they take a minimum of about a month and a half to a maximum of about three months. And within that amount of time, they’ve enumerated your whole network, they have found everything of value. I mean, they have cycles doing this now [so] that they don’t need six months [to] find the valuables. And at the end of that 80 days, everything in your environment is encrypted. Right. And that takes us back to all the different opportunities, we had to detect them and stop it before the ransomware hits.
[Greg] Right goodness.
17:49
[Paul] And I would say the maturity of the organization, right, and the security that they have, and the maturity that they have for cybersecurity in their organization would have an effect on that dwell time, right? So you’re looking at some of these smaller organizations with smaller budgets that probably don’t have the same tool sets as some of the larger, you know, organizations have budgets. So when it comes to getting into your environment, and finding everything they need, you know, sometimes that’s being sped up depending on the layers of security that you have in your enterprise.
18:22
[Greg] Awesome. So now what I’m thinking is, we’ve uncovered the fact that if you’re going to build a capacity of a SOC, you kind of need these three areas. That’s great, Joel. And that’s really an organization looking after themselves. I want to explore a bit more about the idea of collective defence.
So hypothetically, we’ve just talked about care and community organizations that got hacked and are effectively ransomwared. If they were both in a collective defence platform, where they were able both had a network detection and response system within their own organizations. And they’re now sharing that information across. How do you think that would have helped them in terms of being able to detect the event before the ransomware hits?
19:18
[Joel] What and I want to address that, I do want to let our audience members know I am a little biased, right? I do work at IronNet. And we are really building this collective defence platform, hand in hand with our partners, right, who we’re helping defend.
But I want to take a step back to a past life. So I used to be a penetration tester, right. And one of my jobs was I had to run phishing campaigns against these organizations. And I wasn’t running them against everybody in their organization, right? I was running them against system administrators or people with elevated privileges in their environments.
And I had my own infrastructure, right. So my own IP with my own fishy domain, right, that was hard to tell the difference right between The legitimate service in my domain, and I would go and I would fish an organization. And you know, if I had 50 admins, I’d get 30 of them to click my link, sometimes less, sometimes more. But a good amount. Greg, the crazy part is, I could move on to my next penetration test with a different organization, I can use that same domain or IP, and I can still get 2030 clicks of admin level users. So here’s what I’m saying:
“Imagine if those organizations could have worked together to say, Man, we got fished, we got bit, rate it malicious, and that has now correlated to the community?”
So if that domain is even ever seen, immediately, they know, it’s fishy, immediately, they can isolate it, or they can even use their API’s to quarantine and send those to spam or trash, right? So there’s a lot around that. But when we talk about collective defence, it’s not just about fishing, this is about advanced behaviours, right? those behaviours on the network that we talked about the dark side group using before they execute ransomware. Now we can share those behaviors across the world as well to help defend organizations.
21:12
[Greg] Well, so what might have been, hey, so [they] could have that? [So] the tricky thing is how to detect things in that stealth mode, when the bad actors have got some sort of a leverage into your network. But they’re not [where they want to be] yet. And they’re trying to expand their leverage to be able to affect as much as they can. How do you detect people, or organizations or people in that mode, and then share that with other people? Because it’s expensive, right? Building a SOC, and to have all this capability. So just, there’s another aspect of that, which is what I’m thinking is, how do we have that benefit of getting that expertise from other organizations who are dealing with the same issues, and they’re having their own responses to that? It would mean that your SOC doesn’t need to be as many people in it? It can be, it’s faster for those people to make a great decision on what’s the best way to remediate. And so the whole organized across the whole sector benefits from this. Is that what you guys are seeing?
22:21
[Joel] Yeah, so I want to, I want to kind of, you know, before we start pulling SOC analysts out of the SOC, you know, not have to dress we have to get good at stopping these threat actors, which I don’t believe anybody really is good at now. Yes, we are helping streamline things. So when incidents are seeing certain behaviours, certain indicators are seen, there’s already somebody, chances are somebody around the world has seen those and has been able to look at them, triage them, maybe add comments on them, right?
And now those can be correlated to:
- “Hey, it’s either benign, you don’t have to worry about this” to
- “Yes, it’s showing, you know, anomalous weird behavior”, or
- “Hey, this is suspicious. I don’t know what it is”, or
- “No, it’s definitely bad”.
Right? So having, you’re giving your SOC analyst, I, once again, the experiences vary around the world right here in the US, we’re blessed with some very top-tier talent. I know other countries in the Middle East, Europe, they have difficulty finding talent like that.
But imagine if you could work together around the world, and leverage different security capabilities, different analysts skill sets in real-time to help prevent this stuff. It’s a powerful concept. And that’s what we’re working towards.
23:33
[Paul] And that process as well helps you prioritize what you need to look at inside your own environment, right? So, you know, you always hear around alert fatigue and trying to filter out what your SOC analyst needs to look at and the level of experience, they have to look at certain behaviors inside your environment as well. So being able to almost crowdsource other SOC experts, you know, across different, you know, across your ecosystem across at a national level, or even through five eyes, right, is going to benefit your organization.
24:09
[Greg] That’s awesome. Well, thank you, Paul. Thanks, Joel. So if you’re listening to this, we’re doing this as part of the build-up the ramp-up to an Australian caring community. IronDome, is a platform that does its collective defence, we believe is going to make a really big difference in the sector.
For those who are the most vulnerable in our community in the Australian society and the New Zealand society can benefit from this shared cyber-defence to that, that we can keep delivering great scam care and community services to them without fearing of cyber-attack or cyber threat to those people. If you want to know more, we’re launching a trial of this platform in the second half of 2021. We’d love for you to reach out to us and put your hand up to be a part of that trial and see the banner First, and then when we can prove this thing as saying it actually works, it actually produces value, then we were able to scale it out and protect the whole sector. If you want to find more about each one of us, perhaps I’ll throw to you, Joel, what’s the best way to stay in contact or to watch what you’re doing?
25:17
[Joel] Yeah, so I stopped each of you guys on LinkedIn before this. So I know everybody on here has a LinkedIn. But please, like we want to make these chats inclusive to the community. So if you are seeing this, if you are interested, like reach out to us on LinkedIn, ask us a question. We can keep it anonymous if you want, but we’d love to bring your question into the next talk. Let’s get your guys’ questions answered. And I’m really excited, Greg, thanks for having me on. I’m really looking forward to interacting with the Australian community.
25:43
[Greg] Excellent. And so LinkedIn Best for Joel. Paul is anything else you want to add in following you or finding you on the internet?
25:50
[Paul] No, I think what Joel’s pretty much put out there with LinkedIn is probably a good option. So, um, you know, we’ve been, you know, working very closely with you, Greg, yourself for Network Overdrive. So even if you have questions, filter them through Greg to us, or, as Josh mentioned, just ping us on LinkedIn.
26:10
[Greg] Excellent. So we hope to have this as a regular event. I want once a month update just reviewing the security events around the world of particularly in Australia and New Zealand and how they relate to the care and community sector. We’ll say goodbye for now. Thanks for listening in and we’ll keep you posted next time.